Symfonos 5 CTF is based on the web application exploit and ldap information gathering to get to the root. This is an easy CTF, but good learning cracking this CTF.
The Stuff I have learned is to use ldpsearch and fpm during this CTF .
Let’s start the walkthrough!
I used Symfonos in a vmware. You can use netdiscover to get the IP of the machine.
Next thing is Nmap to check the open ports on the machine.

So we have ports 22,80,389 and 636, which are pretty much needed to get inside the system.
If you check the website, there is a static image all over the front.

I have checked the source but I do not find anything useful.
then I ran Dirb to check for useful urls and I got admin.php.

admin.php asks for login credentials.

I checked these field with some common username and password manually. I also checked for SQL injection, but then I remembered we have ldap here. So I started searching links for the ldap injection so we can bypass this login form.
I have tried most of them but didn’t get access. Then I thought of trying ‘*’ Asterisk on both the fields and turns out it worked!
So we are on home.php page which has under Development written.
When you check the source code for the page, you will find a little info about the get variable it takes and it render its output.
If you see in the above source, home.php?url=http://127.0.0.1/portraits.php,this gives us power to perform LFI [Local File Inclusion] so we can check what are all the code there.
If I write ?url=admin.php, I can get the information of admin for this.

There we go, We have information about web ldap user here and dc components of the ldap to make our search easier.
Now, let’s do ldapsearch.
“ldapsearch -D “cn=admin,dc=symfonos,dc=local” -w qMDdyZh3cT6eeAWD -p 389 -h 192.168.132.129 -b “dc=symfonos,dc=local” “

This gave us username and password of the local user which is Zeus.
The UserPassword: Y2V0a0tmNHdDdUhDOUZFVA==, this is in base64.
After decoding it we will get : cetkKf4wCuHC9FET
Now we can ssh this.

I looked around but didn’t find anything that i can exploit.
Next thing is to check SUID. I typed sudo -l:
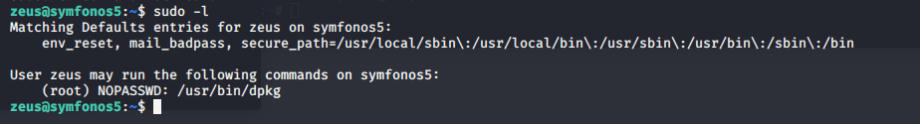
Now, we know if by any chance we can run dpkg file with a shell we can have root access.
I searched a bit about it and here is a good link I found:
https://lsdsecurity.com/2019/01/linux-privilege-escalation-using-apt-get-apt-dpkg-to-abuse-sudo-nopasswd-misconfiguration/

our file is all ready, all we need to do right now is to copy this to the Zeus account in Symfonos.
SCP will do this job for us:

That’s Done!
Time to run this file and have root access:

that’s it!
If you are interested in SQL injection for base64 encoded string follow this link : http://www.anonhack.in/2018/10/sql-injection-on-base64-encoded-string-parameters/
