This article will guide you on how you can bypass the POST reflective HTML injection in Bwapp. This is similar to the GET request and again we don’t need burpsuite as a mandatory tool. It can be easily done with the help of a browser. I have used firefox with hackbar tool called URL encoder, which encodes the special characters in URL encoding.
Let’s get on with the task:
To check I have written <h1>hack by <h1> and in password <h1>3rz5ebe7</h1> .

As you can see below, the output is reflected as it is. So here we need to bypass the filter it is taking.

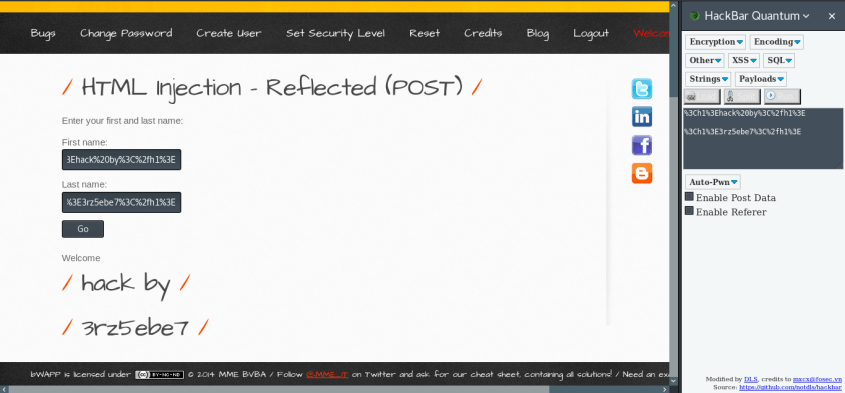
I copy pasted the injection code in the hackbar on the right side.

In the options, select the injection code and then select the Encoding as Url Encode. This will encode the angular brackets and splashes.

See the output in the below screenshot. The encoded string will look like this.

I encoded both and paste them in the first name and last name fields. HTML injected code works.
With this vulnerability, you can manipulate the page and insert form or inject certain malicious code so that with user interaction we can get the information about the user.
